DNS - performance optimization and security
The main task of DNS (Domain Name System) is to translate domain names to IP addresses (e.g. www.endevel.cz to 161.35.202.7). Without addressing, communication between users would not be possible. Instead of users having to remember IP addresses, today we use readable domain names. The job of DNS is to convert human-readable domain names into machine-readable form. In this article, we'll describe the main DNS functions and explain the basics of DNS performance and security.
How DNS works?
DNS servers
Due to the amount of data that must be stored for domain name resolution, the DNS database is distributed over a large number of servers. The main purpose of the servers is to store DNS records and to provide responses to client queries. According to their role in the DNS system, we can divide them as follows:
- Recursive DNS server (also resolver): This type of server is responsible for resolving client queries by recursively querying other DNS servers.
- Authoritative server: Provides authoritative information for the domain names it serves, such as the IP address for a specific domain name. It is in charge of one or more parts of the domain namespace (DNS zones).
- Cache server: After resolving the DNS query, it temporarily stores the DNS records in the cache. It is used to optimize the domain name resolution process.
- TLD server: It is responsible for top level domains, e.g. .com, .org, .cz.
- Root server: It is responsible for providing information about the root zone of the domain namespace. Every recursive lookup process starts here.
DNS resolution
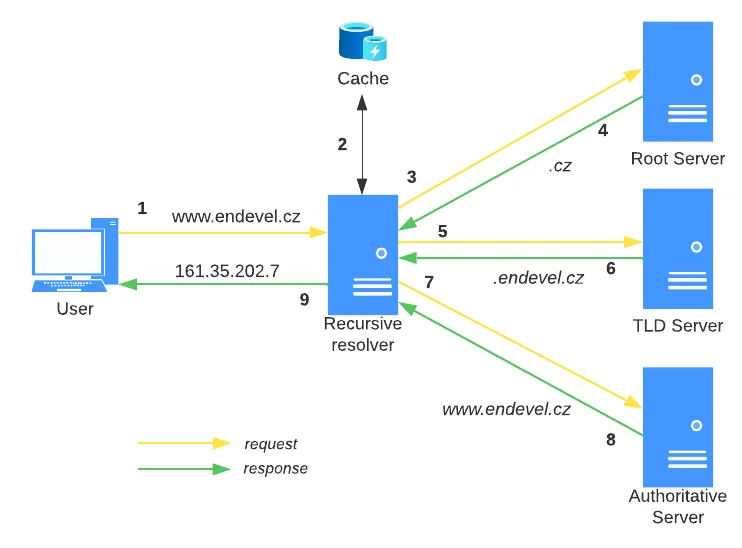
Resolution process
- The client requests the IP address for www.endevel.cz from the local recursive DNS resolver.
- The resolver first checks if it already has the answer in its local cache.
- If it did not find an answer in the cache, it requests an IP address from the root server.
- As a response, the root server sends back the IP address of the TLD server (.cz).
- Using this IP address, the resolver requests an IP address from the .cz name server.
- The TLD server (.cz) sends back the IP address of the name server of the .endevel.cz domain.
- Using this IP address, the resolver requests the IP address for www.endevel.cz from the name server .endevel.cz.
- The name server .endevel.cz sends back the IP address for www.endevel.cz to the DNS resolver.
- The resolver sends the requested IP address of www.endevel.cz back to the client - 161.35.202.7.
Performance optimization
The resolution process can have a significant impact on the performance of web applications. Various methods and techniques are used to optimize DNS services to increase overall performance. Improving the performance of web applications may include reducing the time it takes to resolve domain names or reducing the latency of client requests.
DNS Caching
DNS Caching is a process that is used to speed up the resolution process. Caching DNS lookup results can reduce the load on DNS servers. When a DNS resolver receives a request to resolve a domain name to an IP address, it first checks to see if it has a copy of the domain record stored in its cache. If it finds one, it immediately returns the result (the IP address) without recursively looking for the answer and querying the authoritative DNS server.
DNS TTL (Time To Live) is a setting that determines how long a record will be cached. When the timeout expires, the resolver must resend the domain record request. A shorter TTL means more requests and more accurate results, while a longer TTL means fewer requests but also often incomplete and less accurate results. The TTL can be set according to the needs of the application, and the value of this setting can also have a significant effect on the DNS propagation delay. It is important to configure the cache correctly to avoid excessive storage of outdated information and to secure web application against potential attacks (see below).
DNS Prefetching
DNS Prefetching is a technique used by web browsers to actively resolve domain names that a user is likely to visit while using an application. By prefetching the DNS record, the browser can speed up the overall page load time.
When a user visits a web page, the web browser scans the HTML content for all domain names, sends requests to the extracted domains, and caches the results. When a user clicks on a certain link, the IP address is read from the cache without having to resend the lookup request.
Round-robin DNS
Round-robin DNS is a load balancing technique that aims to distribute traffic across multiple servers. In response to a domain name resolution request, the authoritative DNS server sends a list of multiple IP addresses (in random order) associated with that domain name. The DNS resolver then returns the list of IP addresses to the client, which uses the first IP address in the list to connect to the web server. The next IP address from the list is used for the next client request. When the end of the list is reached, the first IP address is used again. The main disadvantage of this method is the lack of full load balancing, which is mainly due to DNS caching and client-side caching.
DNS Security
The original implementation of DNS did not include any security features. Since DNS is a public service and is available to every Internet user, it is exposed to many attacks. Attacks can compromise web servers and systems, making fast and secure DNS communication impossible.
Some of the most common types of attacks that can occur on a DNS system are:
- DNS spoofing/cache poisoning is an attack where fake data is injected into the DNS resolver cache, which causes the resolver to return, for example, the wrong IP address for the searched domain. The attacker can thus redirect the user to another website, where the user can enter his credentials or download malicious content (computer worms, viruses, etc.)
- DNS hijacking is an attack similar to DNS spoofing, but in this case it's not about spoofing the resolver cache, but targeting the web application's DNS records on the DNS server. If an attacker manages to hack a DNS server, intercept communication between a user and a DNS server, or otherwise change DNS settings, he is able to redirect a DNS query to another DNS server, giving the user the IP address of a fake website as a response to the query.
- DNS tunneling uses the DNS protocol implementation to tunnel malware. Through DNS queries, it enables the establishment of a connection between the client and the attacker's server and subsequently infiltration/exfiltration of data or remote control. Since most DNS traffic can pass through a firewall, an attacker is able to create a communication channel that bypasses most firewalls, making this type of attack difficult to detect.
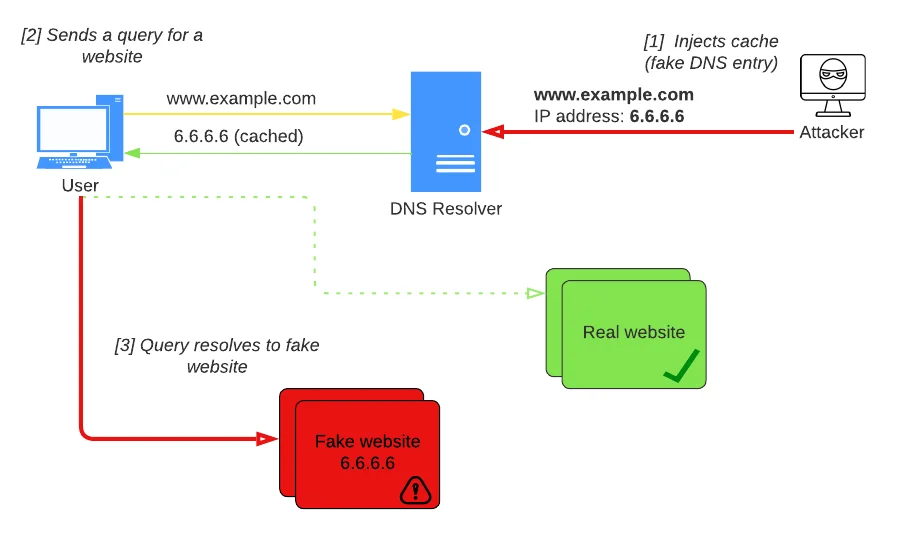
DNS cache poisoning - example of an attack
- An attacker poisons the DNS cache (most often by impersonating a valid DNS server, sending a request to a DNS resolver, and then forging a response to a DNS resolver query). For the domain name www.example.com, the IP address (6.6.6.6) of the fake website is returned.
- The user sends a lookup request to the DNS resolver to resolve the domain name (www.example.com) of the desired website.
- The user receives a fake website address from the DNS resolver, resulting in a connection to the attacker's website.
DNSSEC
One of the main ways to secure the DNS system is to implement DNSSEC (Domain Name System Security Extensions). DNSSEC is a security protocol that was created to protect the DNS infrastructure. This DNS extension is based on the principle of signing DNS messages.
Using public and private keys (asymmetric cryptography), DNSSEC is able to ensure authentication and data integrity. It also serves to verify that the DNS server is trusted by a higher domain in the DNS hierarchy (the so-called chain of trust).
When using the DNSSEC extension, each response to a DNS query in the resolution process contains a signature (RRSIG - resource record signature), which the DNS resolver is able to verify using a public key (DNSKEY record). DNSSEC secures traffic and makes it much harder for attackers to spoof or manipulate DNS responses.
DNSSEC is usually used in combination with other methods and techniques for full DNS protection, such as implementing DNS filtering, DNS firewalls, and actively monitoring DNS traffic.


